Experimenting with Encrypted Client Hello (ECH)

One day I was reading the news and come across an article that China has blocked all ESNI-related traffic because it serves as an effective tool for censorship circumvention it made me intrigued because of the way it was blocked.
Normally, their censorship relies on filters like Transparent Proxies, DPI, and similar things, but this instance is a bit severe because it simply blackholes all traffic using TLSv1.3 and ESNI which means the protocol works as intended by making snooping SNI value hard.

I live in Indonesia, where the government similarly imposed censorship using techniques like reading SNI values, keyword matching, and deep packet inspection.
Although I can see some of the justifications for censoring, I'm always uneasy about the fact that your ISP and the government can see what you're currently browsing.
Despite the fact that I almost always use VPNs, they occasionally make my work more difficult, either due to slow speeds or the overzealous Firewall that prevents connections from almost all VPN servers.
It points back to ECH, which takes the place of Encrypted SNI as a solution to plug some security gaps with TLS and SNI.
Browser Support
Mozilla champions ECH along with Cloudflare and others, so ECH is deeply integrated well with Firefox since version 85+
It is supported for Chrome, Edge, and other Chromium-based browsers starting with version 105+, however, the feature is still only partially supported for most of them so your mileage may vary.
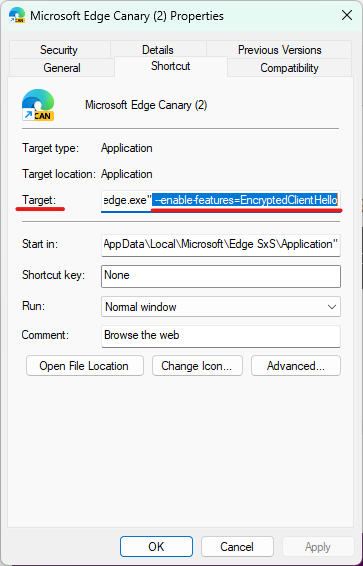
Setting up ECH
Since Firefox was the browser I used on a regular basis, I'll be using it in this tutorial.
Before we begin, we'll use this convenient URL created by Tolerant Networks to verify if ECH is enabled as a benchmark.
https://defo.ie/ech-check.php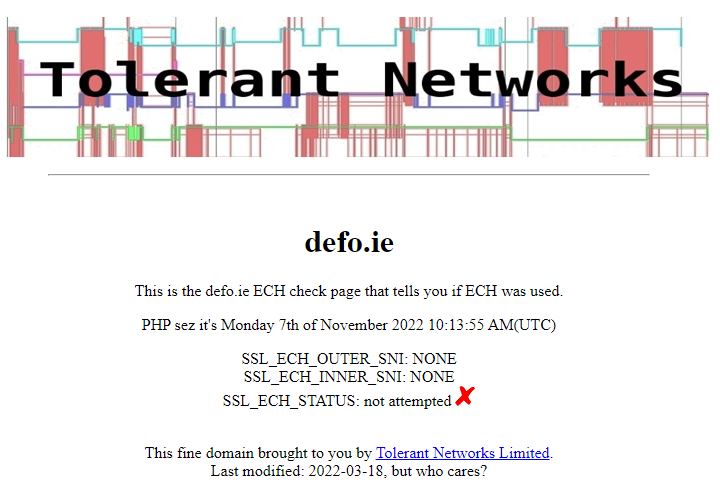
As you see, the browser wasn't attempting to encrypt the client's hello message.
To fix that, we'll make sure to enable DNS-over-HTTPS (DoH) first by accessing the settings menu.
Settings -> General -> Network Settings
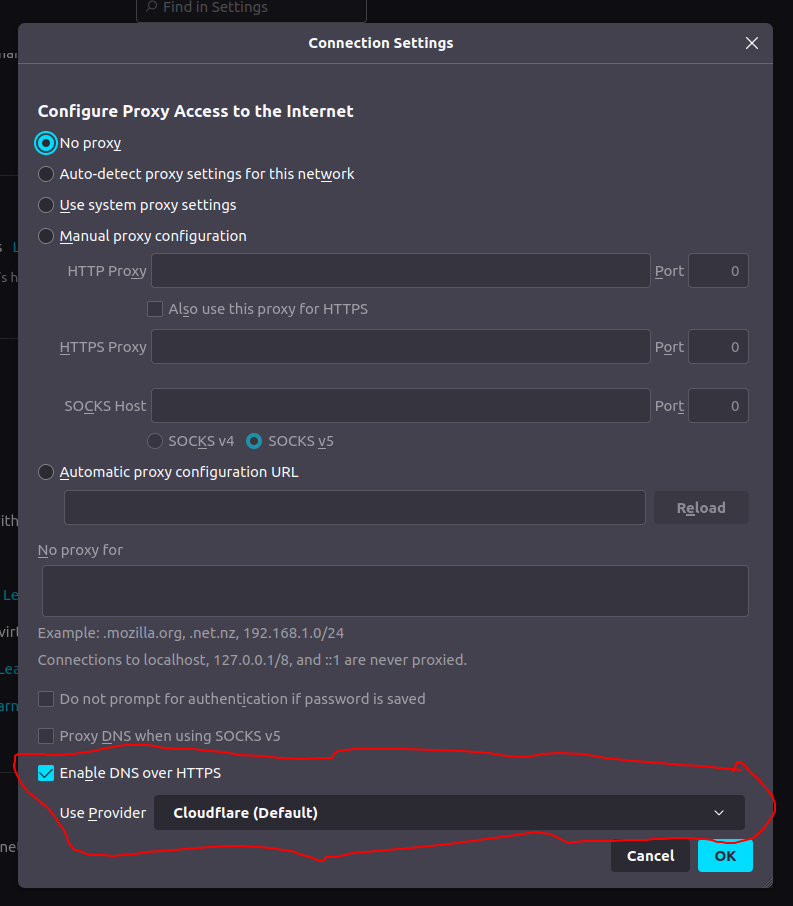
We will set the provider to Cloudflare, as they are one of the major operators of ECH-enabled servers and networks.
Next, to enable ECH we need to change two config variables by accessing the about:config page.
network.dns.echconfig.enabled = true
network.dns.use_https_rr_as_altsvc = trueAfter changing both values, to make sure the configuration is applied I restarted my browser and re-checking the ECH check page.
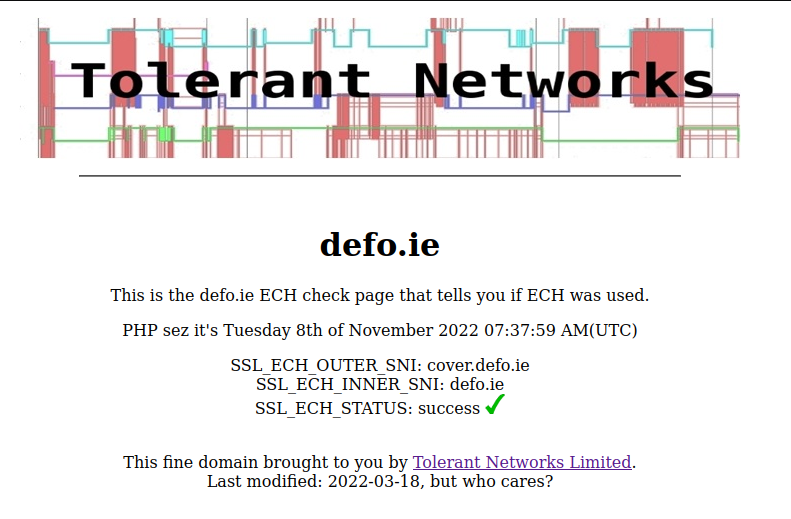
Voila! The browser now attempting to encrypt the SNI value.
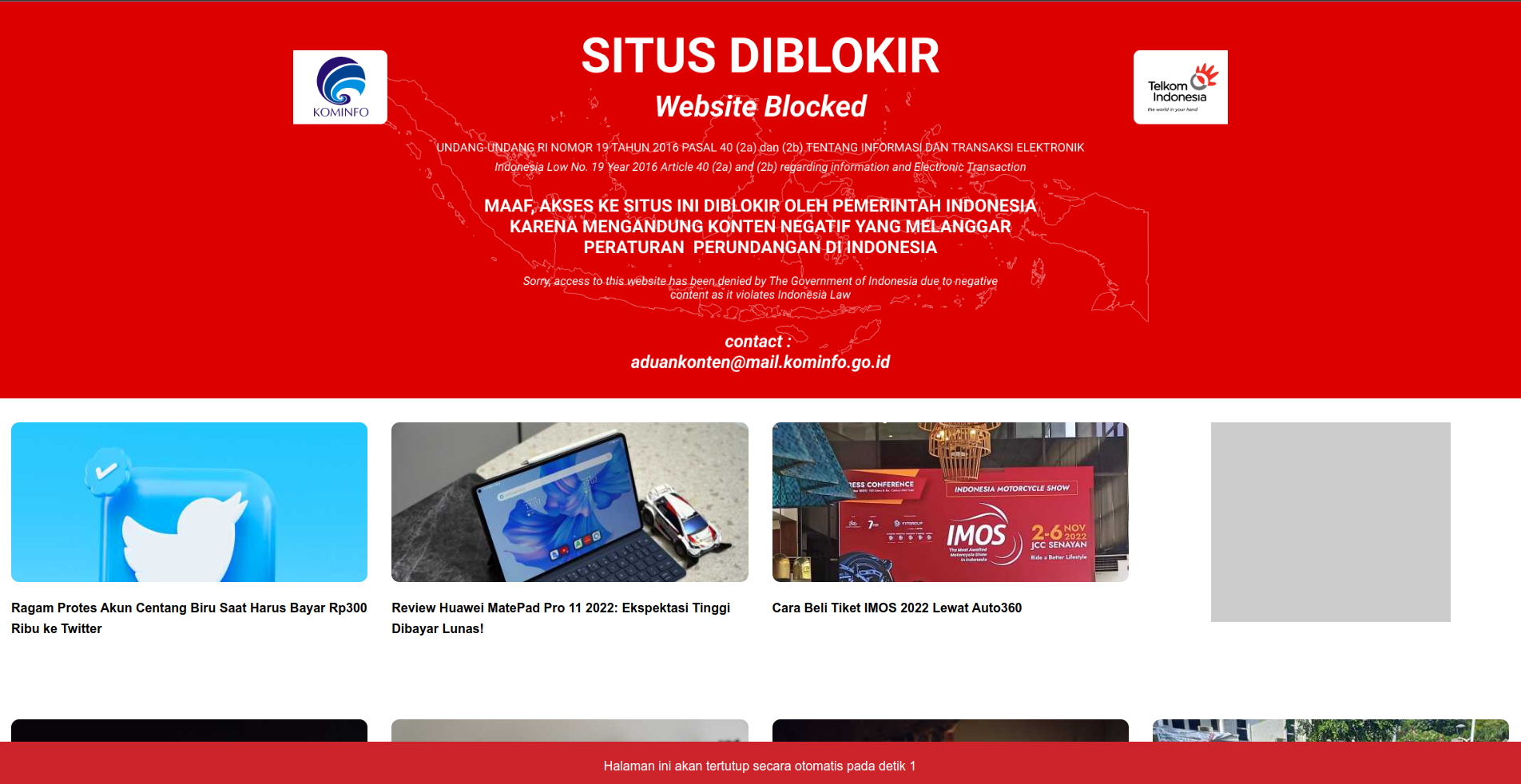
One of the pages I tried accessing is ThePirateBay, which for you who don't know mostly hosted a lot of pirated content and has been blocked and censored in Indonesia.
Conclusion
Although it isn't a privacy cure-all, ECH helps to address many problems with TLS in general in the age where governments are leveraging its vulnerability to spy on people, gather user data, and impose censorship.
Although it won't soon replace my VPN, it is one of the more effective solutions for enhancing user privacy, and I can't wait for it to be used more widely.
Read More about ECH




