Setup Traefik as a systemd Service
This guide will help you set up Traefik as a systemd service, with detailed instructions on configuration, and examples.

Traefik is a reverse proxy and load balancer that I love for both work and personal projects. It's versatile and can be deployed in various environments such as Kubernetes, Nomad, and more.
But sometimes, you want to keep things straightforward, like setting up a dedicated load balancer on its VM without all the extra fuss of containerization or complex virtual networking. In this article, I'll walk you through configuring Traefik as a simple systemd service.
Initial Setup
To start, grab the most recent version from GitHub. As of this writing, version 3.3.4 is the latest, so I'll be using that for this guide.
curl -L -O https://github.com/traefik/traefik/releases/download/v3.3.4/traefik_v3.3.4_linux_amd64.tar.gzExtract the downloaded file, move it so it can be executed system-wide, and set the required ownership and permissions.
tar -xvf traefik_v3.3.4_linux_amd64.tar.gz
sudo mv traefik /usr/local/bin
sudo chown root:root /usr/local/bin/traefik
sudo chmod 755 /usr/local/bin/traefikAllow Traefik to bind port 80 and 443 as non-root user.
sudo setcap 'cap_net_bind_service=+ep' /usr/local/bin/traefikCreate a new dedicated user and group for Traefik.
sudo groupadd -g 321 traefik
sudo useradd \
-g traefik --no-user-group \
--home-dir /var/www --no-create-home \
--shell /usr/sbin/nologin \
--system --uid 321 traefikIf you're running docker as non-root and want Traefik to have access, add the user to the docker group.
sudo usermod -aG docker traefikSetup default static configuration
Next, set up directories and permissions for storing the configuration files.
# static configuration and default logging
sudo mkdir /etc/traefik /var/log/traefik
sudo chown -R root:root /etc/traefik
sudo chown -R traefik:traefik /var/log/traefik
# dynamic configuration and acme stores
sudo mkdir /etc/traefik/acme /etc/traefik/dynamic
sudo chown -R traefik:traefik /etc/traefik/acmeCreate a new static configuration file in /etc/traefik/traefik.toml with the following entry.
[entryPoints]
[entryPoints.web]
address = ":80"
[entryPoints.websecure]
address = ":443"
[log]
level = "DEBUG"
filePath = "/var/log/traefik/traefik.log"
[accessLog]
addInternals = true
filePath = "/var/log/traefik/access.log"
bufferingSize = 100
[providers.file]
directory = "/etc/traefik/dynamic/"
watch = trueTraefik default static configuration in /etc/traefik/traefik.toml
Set owner and permission for the newly created Traefik configuration
sudo chown root:root /etc/traefik/traefik.toml
sudo chmod 644 /etc/traefik/traefik.tomlConfigure systemd service
Create a new file in /etc/systemd/system/traefik.service and insert the following content
[Unit]
Description=Traefik
Documentation=https://doc.traefik.io/traefik/
After=network-online.target
Wants=network-online.target systemd-networkd-wait-online.service
AssertFileIsExecutable=/usr/local/bin/traefik
AssertPathExists=/etc/traefik/traefik.toml
[Service]
# Run traefik as non-root user
User=traefik
Group=traefik
# Additional security directives
CapabilityBoundingSet=CAP_NET_BIND_SERVICE
AmbientCapabilities=CAP_NET_BIND_SERVICE
NoNewPrivileges=true
# configure service behavior
Type=notify
ExecStart=/usr/local/bin/traefik --configfile=/etc/traefik/traefik.toml
Restart=always
LimitNOFILE=1048576
# lock down system access
# prohibit any operating system and configuration modification
ProtectSystem=full
# create separate, new (and empty) /tmp and /var/tmp filesystems
PrivateTmp=true
# make /home directories inaccessible
ProtectHome=true
# turns off access to physical devices (/dev/...), when running on RPi disable this
PrivateDevices=true
# make kernel settings (procfs and sysfs) read-only
#ProtectKernelTunables=true
# make cgroups /sys/fs/cgroup read-only
#ProtectControlGroups=true
# allow writing of acme
ReadWriteDirectories=/etc/traefik/acme
[Install]
WantedBy=multi-user.targetTraefik systemd service file in /etc/systemd/system/traefik.service
Next, set the correct owner, permission, and enable the service at startup
sudo chown root:root /etc/systemd/system/traefik.service
sudo chmod 644 /etc/systemd/system/traefik.service
sudo systemctl daemon-reload
sudo systemctl enable --now traefik.serviceTraefik should be running, you could check the service status by executing:
sudo service traefik status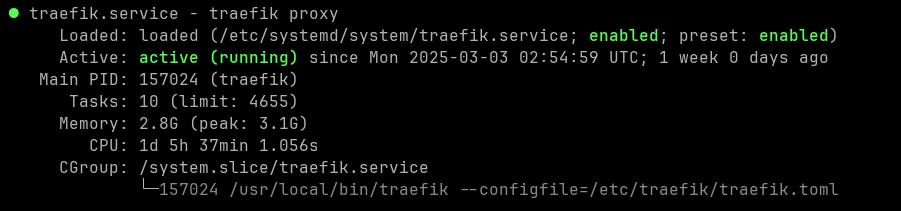
Wrapping Up
If the service is operating, you have successfully set up and configured Traefik as a systemd service, and I hope this guide was useful and made things easier for you.